SENSOR DATA SECURITY
Should you have any questions or queries, feel free to reach out to us at: info@iox-connect.com
IMPORTANT
ioX-Connect Wireless Sensors have been designed and built to securely manage data. ioX-Connect works to ensure your data security is handled with the utmost care. The same methods utilized by financial institutions to transmit data are also used in ioX-Connect's security infrastructure. Security features from sensors to gateways include tamper-proof network interfaces, data encryption, and bank-grade security.
The proprietary sensor protocol uses low power and specialized radio equipment to transmit application data. Wireless devices listening on open communication protocols cannot eavesdrop on sensors. Packet-level encryption and verification is key to ensuring data traffic isn't altered between sensors and gateways. Paired with a best-in-class range and power consumption protocol, all data is transmitted securely from your devices, ensuring a smooth, worry-free experience.
How Sensor Encrypt-RF Works
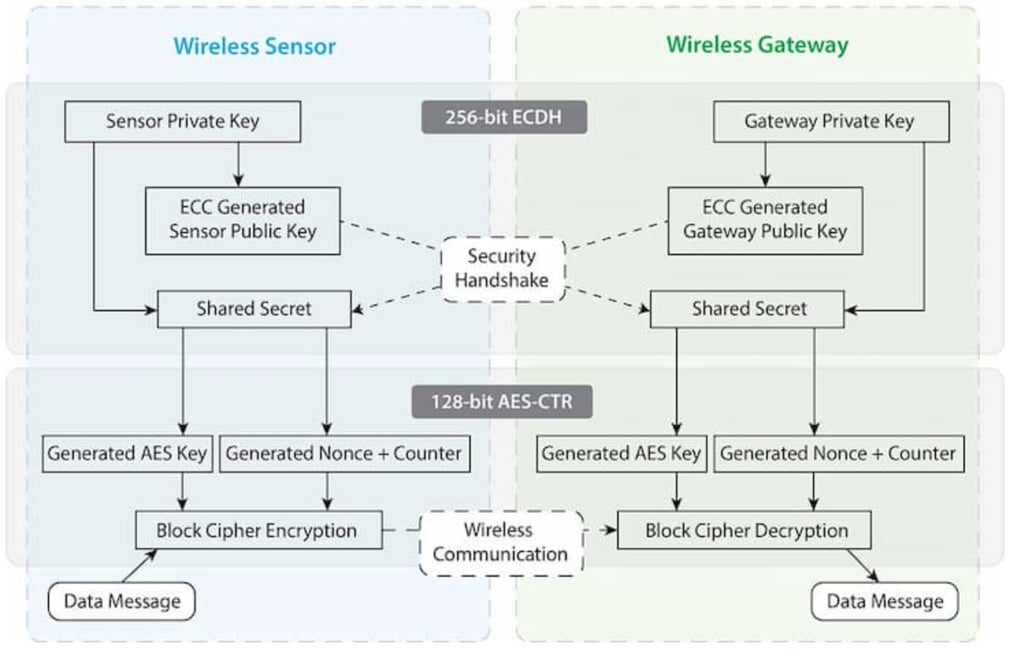
Sensor Communication Security
The sensor-to-gateway, secure wireless tunnel, Encrypt-RF™ , is generated using ECDH-256 (Elliptic Curve Diffie-Hellman) public key exchange to generate a unique symmetric key between each pair of devices. Sensors and gateways use this link-specific key to process packet-level data with hardware-accelerated 128-bit AES encryption, which minimizes power consumption to provide better battery life.
Sensor Gateway Data Security
ioX-Connect Sensor Gateways are designed to prevent prying eyes from accessing the data that is stored on the sensors. Gateways do not run on an off-the-shelf, multi-function operating system. Instead, they run on a purpose-built specific, real-time, and embedded state machine that cannot be hacked to run malicious processes. There are also no active interface listeners that can be used to gain access to the device over the network. The fortified gateway secures your data from attackers and secures the gateway from becoming a relay for malicious programs.
Data Security on the Sensor Portal
The ioX-Connect platform is the online software and central hub for configuring your device settings. All data is secured on dedicated servers operating Microsoft SQL Server. Access is granted through the ioX-Connect user interface with custom URL's, Single-sign-on (SSO), or an Application Programming Interface (API) safeguarded by 256-bit Transport Layer Security (TLS 1.2) encryption. TLS is a blanket of protection to encrypt all data exchanged between ioX-Connect applications and you. The same encryption is available to you whether you are a Basic or Enterprise user of ioX-Connect software. You can rest assured that your data is safe with ioX-Connect.
Additional Data Authentication
SensorPrints is an industry leading end-to-end Internet of Things data authentication method for low-power wireless sensors. SensorPrints authenticates data by issuing a unique fingerprint for each device within the IoT. Data is secured from the point of generation to the point of consumption. Easy to install and use, SensorPrints is the definitive loT security solution for any enterprise.
SensorPrints authenticates data at both the point of generation and consumption, creating trust between the sensor and server levels. Implementing 256-bit SHA 3 authentication, SensorPrints creates a "fingerprint" for an ioX Wireless Sensor that contains an authenticated sensor message. When data is transmitted from the sensor, it is accompanied by a generated authentication token. Upon receipt by the application, the token is evaluated via crytographic hash function against a unique per sensor secret key. This step provides an unprecedented level of
full-coverage security for any ioX-Connect customer wishing to secure their loT devices and data.
You can contact us as follows if you have any questions:
EAMS Technologies Inc.
Attention: General Manager
© EAMS Technologies Inc. All rights reserved – Last Revised: November 17th, 2022
